Policy format
AWS' policy documents are JSON-based, with the following syntax:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowBasics",
"Effect": "Allow",
"Action": [
"s3:HeadObject",
"s3:ListBucket",
"s3:GetObject",
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:::1003-green-bucket-1",
"arn:aws:s3:::1003-green-bucket-1/*",
"arn:aws:s3:::1003-green-bucket-2",
"arn:aws:s3:::1003-green-bucket-2/*"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"127.0.0.1",
"127.0.0.2"
]
}
}
}
]
}
In short, the Versions points to which AWS standard the policy follows. Usually it's simply named after the date it was published, and the current default is "2012-10-17". Beneath statement, we find the components which detail what access the keys will have to which buckets, and optionally from where.:
- Sid: Simply a name; make it informative about the policy's function.
- Effect: Keep this at "Allow".
- Action: A list of which s3-actions are allowed. Alternatively, you can assign "*" for everything (examples further down).
- Resource: A list of which buckets the IAM-users shall have access to. Here you'll need to provide the bucket name, and the bucket_name/* for grant access to the underlying objects (see example above).
- Condition: Optional, can be used to add conditions for the access. We usually operate with an IP-whitelist to restrict access from necessary hosts/subnets only.
See Templates for section with more examples to base you policy on.
Creating a policy in the CMC
Navigate to IAM -> IAM policy -> Add New Policy. Similarly as for IAM-users, provide a fitting, informative name, and an path if you'd like (can be left blank):
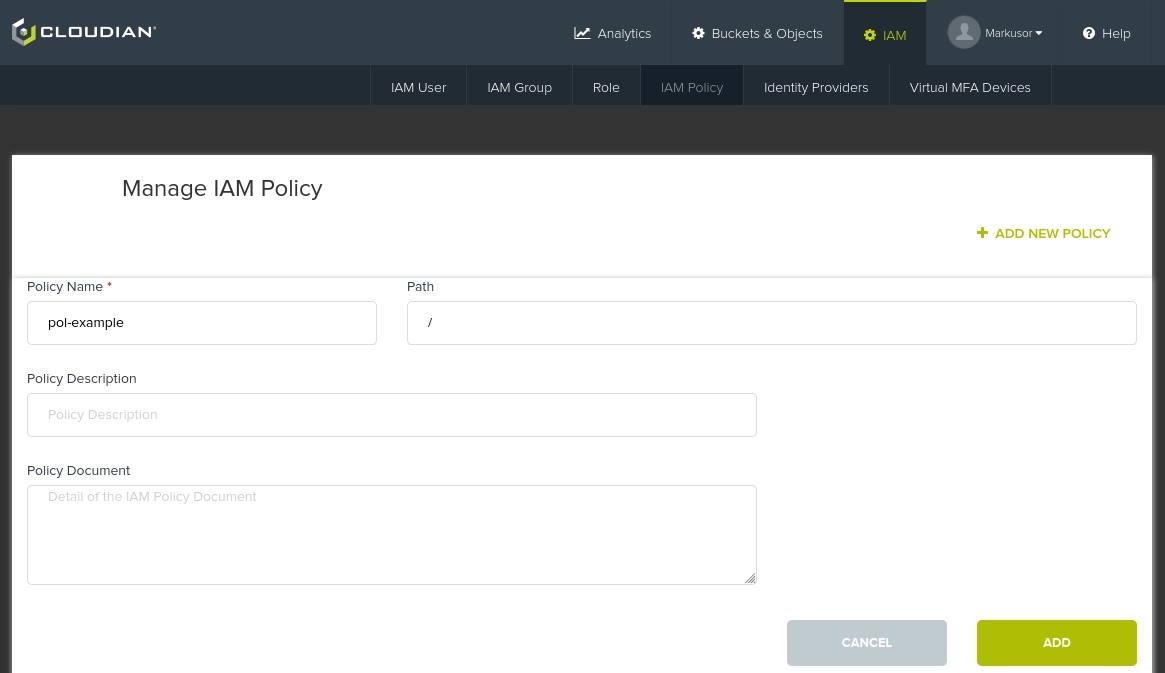
When you click on the "Policy Document" box, a window will pop up providing you with the ability to construct a document using a visual editor.
To begin with, we suggest switching over to the JSON tab, where you will be able to copy in one of our templates.
Example with full access for the bucket"1003-green-markusor-test":
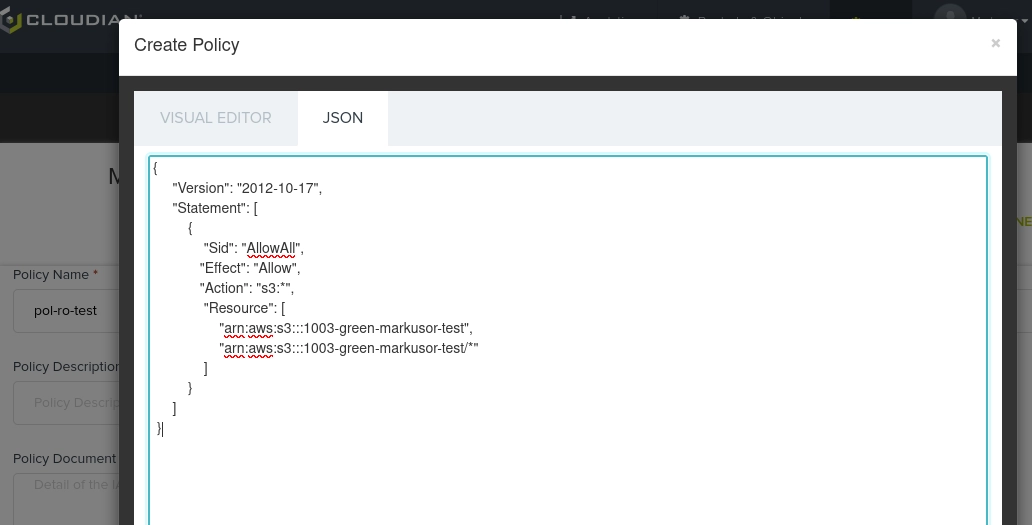
Fill in your details according to the templates, or switch back to "Visual Editor" where the details from the json-document shall be filled in as a starting point.
Attaching policy to IAM-user
After having created a policy; click it and navigate to the "IAM Users" tab.
Click on "+ Attach to user", then you'll have a searchable dropdown menu on the left side where you fill in the IAM user the policy should be attached to:
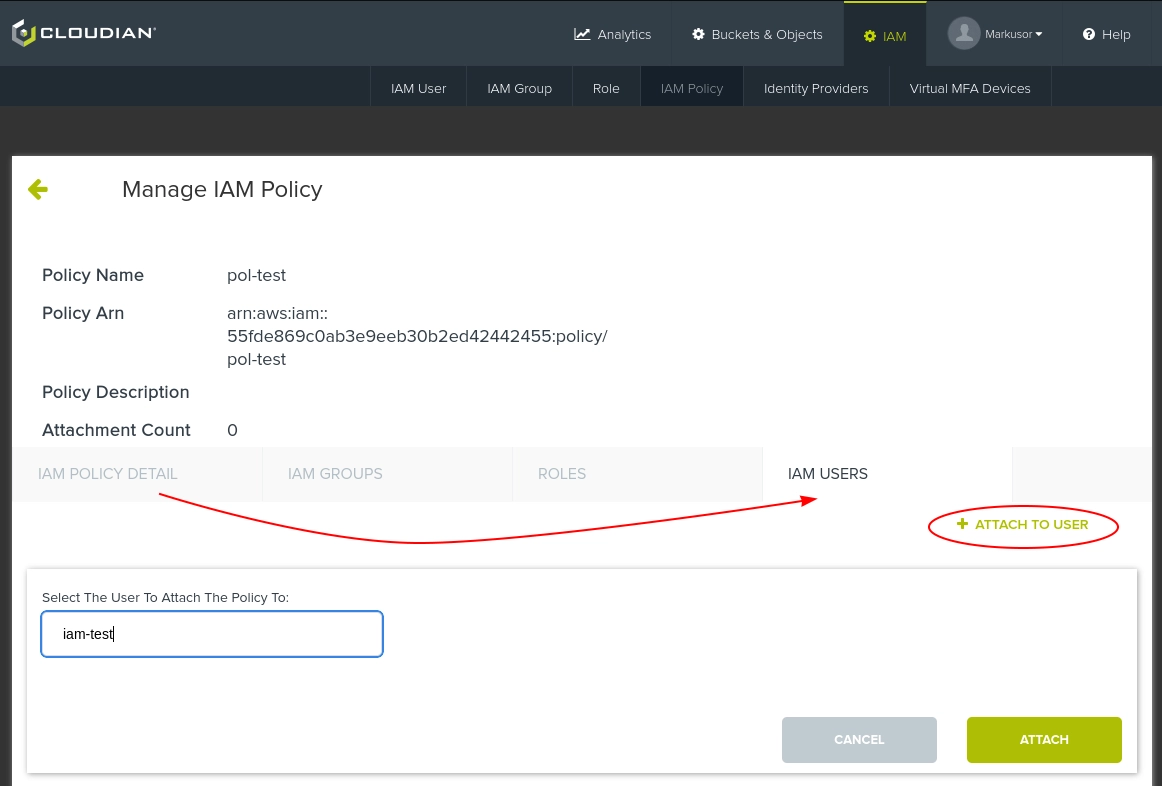
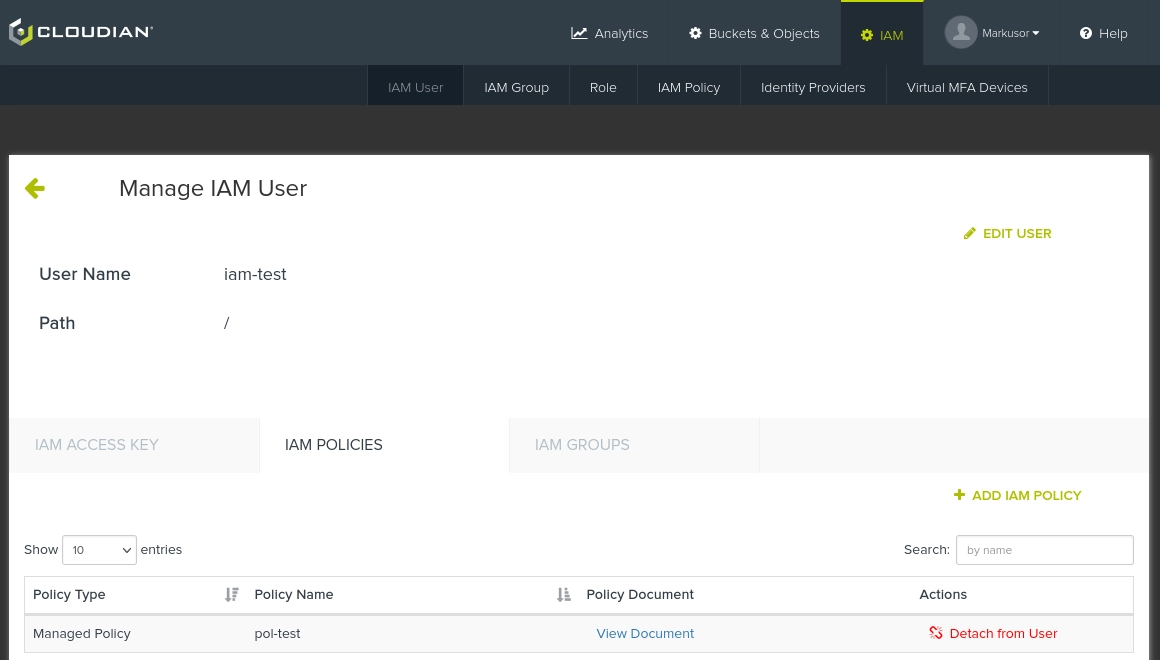
The policy should now be visible as a "Managed policy" at the page of the
IAM user:
Templates
These are .json-documents which can be copy-pasted into the CMC's editing mode as a starting point. Remember to fill in your bucket names and eventual IPs.
For the full list of available s3-actions, see Amazon's doc:
For a clean access regime without the ability to alter ex. metadata attributes, the first example contains the four most used actions for a minimal policy.
If you need extended access, check some examples below.
Full access
Grants access to all s3-actions for selected buckets and from selected IPs.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowAll",
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"<IP 1>",
"<IP 2>"
]
}
}
}
]
}
Read-only
You can also use wildcards (*) to include a selection of s3-actions.
This makes us able to extend to the full list of actions tied to Get, List, and Head for example to create a more extensive read-only policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ReadOnly",
"Effect": "Allow",
"Action": [
"s3:List*",
"s3:Head*",
"s3:Get*"
],
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"<IP 1>",
"<IP 2>"
]
}
}
}
]
}
Write-only
Similarly:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ReadOnly",
"Effect": "Allow",
"Action": [
"s3:List*",
"s3:Put*"
],
"Resource": [
"arn:aws:s3:::<bucket name>",
"arn:aws:s3:::<bucket name>/*"
],
"Condition": {
"IpAddress": {
"aws:SourceIp": [
"<IP 1>",
"<IP 2>"
]
}
}
}
]
}